Benafsh Husain
Data and Visualization Scientist
-
- bhusain@clemson.edu
-
- WEBSITE
- https://husainb.github.io/
I am a 5th year PhD in the joint Computer Science and BioInfomatic degree program at Clemson University with a focus on Bioinfomatics, Data analysis and visualization. My interests lie in using deep learning and machine learning algorithms. My background also invloves image processing and computer vision. Currently, I am trying to learn and explore the field of Deep Learning.
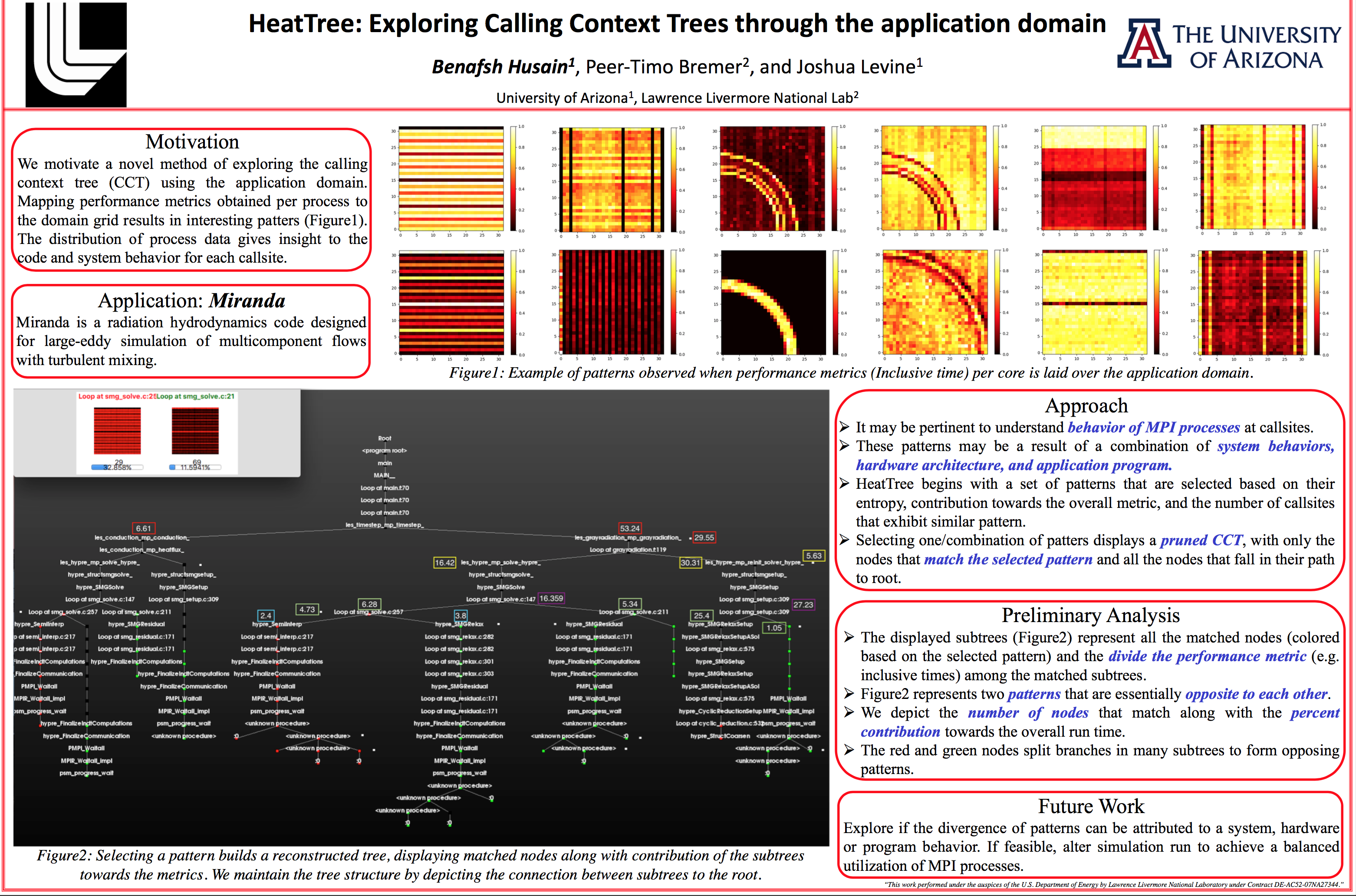
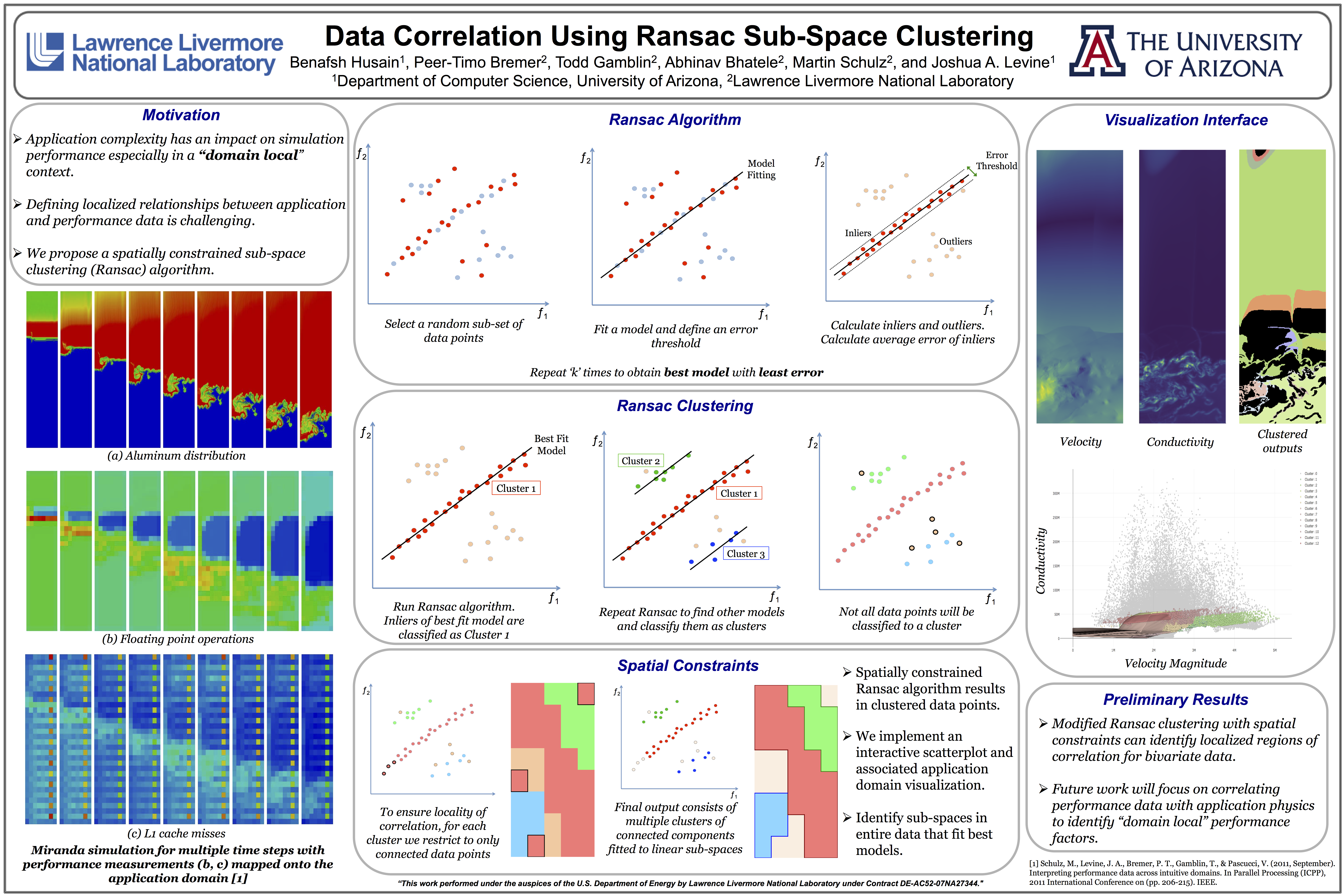
Developed visualization tools to identify performance improvement techniques for scientific application simulations. Identifying and visualizing spatial relationships between application and hardware for multivariate data. Utilized machine learning algorithms to explore correlation between application and hardware domain.
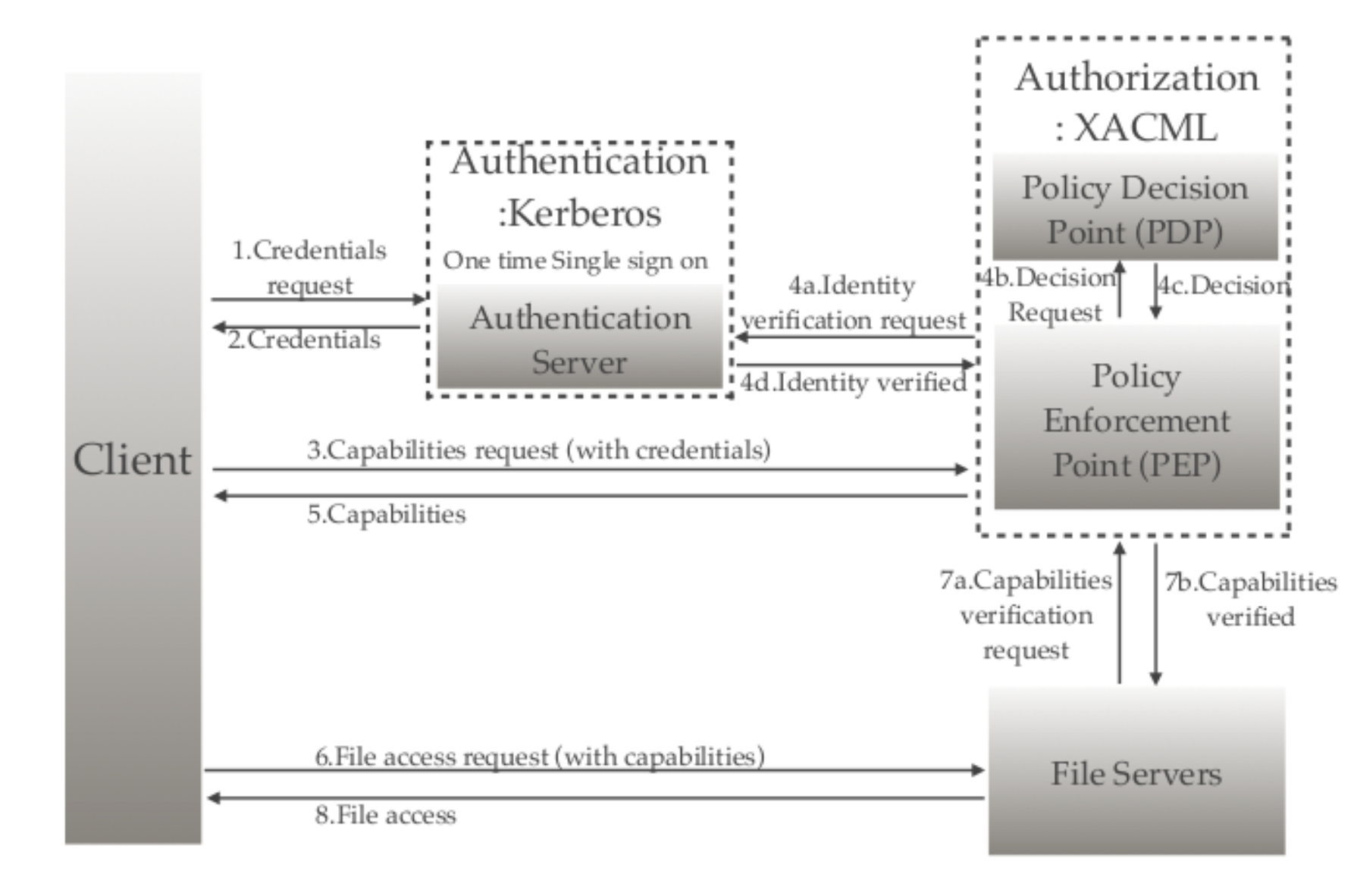
Developed a simulation of an integrated security system over a Light Weight File System written in C. Analyzed the effects of authorization and authentication servers on the timing effects to complete operations such as read/write.
Developing machine learning and visualization techniques to explore multivariate data. Developing visualization techniques and GUI to explore large scale calling context trees.
Project lead in developing system tools assisting academic editors in utilizing a smooth User Interface.
Investigating techniques for lip detection in low quality videos with subjects in moving vehicle. In-depth literature review of existing lip detection techniques and their limitations.
I am currently pursuing my Phd in Computer Science with the focus on data analysis and visualization. This dissertation explores the idea of mapping performance metrics onto a scientific application domain. Using machine learning and visualization techniques, we explore the effects of the application physics on the hardware counters.
My master's thesis focused on Lip detection in low quality videos using a variation of the Viola Jones algorithm. '